Could CryptoWall 4.0 be the biggest threat to your business?
Should you buy a new computer?
May 31, 2016Five ways to find your computer name
June 16, 2016Just a few weeks ago, we posted an article about malware based on the Cryptolocker virus that has been targeting businesses by holding their files for ransom. Since that article was posted, a new version called CryptoWall 4.0 has been discovered, and is actively infecting computer systems across the world.
What’s new?
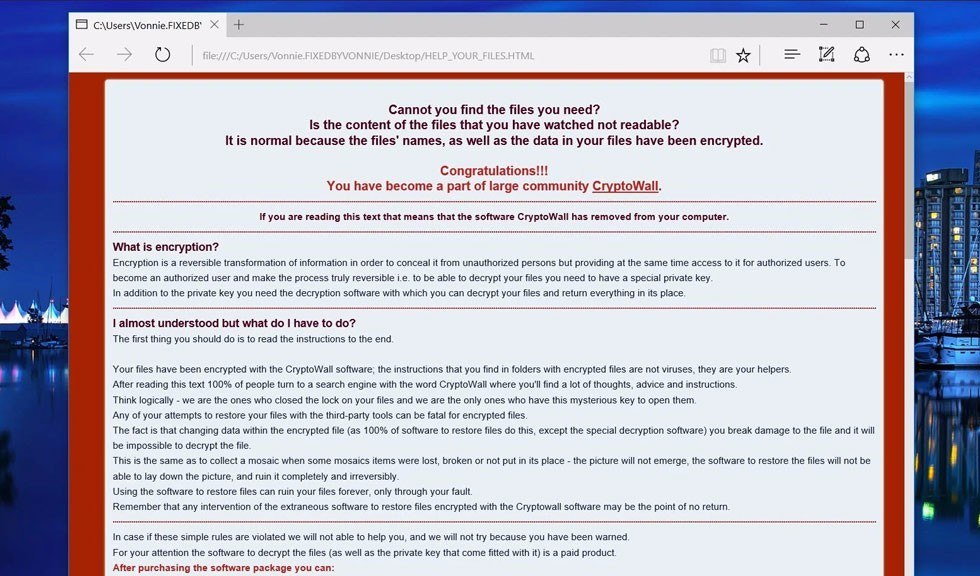
From the perspective of someone whose computer has been attacked by CryptoWall 4.0, not a lot will appear different from previous versions. The malware still acts by encrypting files and demanding a payment in return for providing the decryption key for retrieving the files, although the number has jumped up a bit to $700. There is now some added condescension in its message, as it congratulates you for joining the “large community Cryptowall” before asking you to purchase a “software package” in order to regain access to your files.
This version of CryptoWall also works much more quickly than before. Previously, if users paid close attention to strange behavior from their computer, there was a chance they could catch the virus before it finished encrypting their files. Now, the encryption can happen within less than a minute.
Most of the changes included in the new version are aimed at making the virus harder to prevent, harder to protect, and harder to recover from. These are concerns that your IT team will need to consider when continuing to develop their strategy for securing your network.
How do I prevent it?
Preventing CryptoWall is more difficult than ever. This may be the most dangerous virus in existence right now, solely due to the efficacy of its security system evasion measures. As with previous versions, antivirus software and email and web filtering can’t be relied on to block all attempts at infection. The best way to prevent a CryptoWall attack is to ensure that everyone is informed about the virus and are aware of what practices they should avoid in order to ensure their system remains infection-free.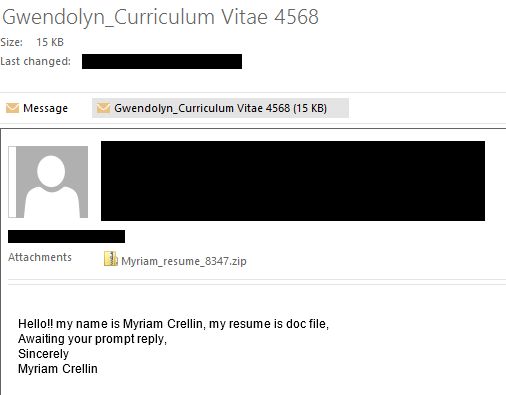
CryptoWall can either be downloaded over the internet, or received as an attachment in an email. Previously, the attachments were either named “resume.zip” or “resume.doc.” In the new version, attachments may also be JavaScript files using the extension *.js that will run an executable file when opened. The subject line of the email is also more likely to follow the following format: firstname_Cirriculum Vitae followed by a four-digit number.
Any files or programs that aren’t from reliable, trusted sources should never be downloaded over the internet. Similarly, emails from unfamiliar addresses, or from trusted email addresses but with strange content, should be treated with a high degree of suspicion. Hiring managers are at particular risk of infection because the virus frequently masquerades as a resume, so they should exercise extreme caution when reviewing applications.
Finally, it’s important that all employees save files on network drives instead of on their local machines, in order to ensure that system backups are accurate and complete.
What happens if I get infected?
Recovering from a CryptoWall 4.0 infection is identical to recovering from any of the previous versions, and relies entirely on recent, external backups having been made of all files. Your IT team will need to remove all files that were installed by CryptoWall, and potentially wipe entire computer systems clean, before reinstalling the operating system and restoring files from backup.
 The immediate reaction to discovering a system has been attacked by the CryptoWall virus must be to turn off all infected computers, contact your IT support, and ensure that nobody accesses the network drives until the IT team has given the all-clear. Even if the virus has encrypted an entire computer, it can still be prevented from encrypting files on the server if the infection is caught in time.
The immediate reaction to discovering a system has been attacked by the CryptoWall virus must be to turn off all infected computers, contact your IT support, and ensure that nobody accesses the network drives until the IT team has given the all-clear. Even if the virus has encrypted an entire computer, it can still be prevented from encrypting files on the server if the infection is caught in time.
Backups must also be kept physically separate from the machine. If an external hard drive used to store a backup is connected to the computer at the time of an infection, the backup can be encrypted as well.
With the release of Cryptowall 4.0, ensuring that your company’s data is regularly backed up is crucial, and should be treated at the highest priority level. If you don’t know whether your recent backups have been successful or not, it may be time to touch base with your IT team and ensure they’re doing everything possible to ensure that your business can recover quickly and completely from a CryptoWall infection.